Protect your plant from OT threats!
Real-time cybersecurity monitoring for OT and critical infrastructures with MON5hield
Evaluate your network infrastructure and OT devices
Request a demo
MON5
MISSION
In an increasingly interconnected world dependent on operational technologies, the security of critical infrastructures is paramount. MON5 is dedicated to protecting production lines from external threats, ensuring operational continuity across a wide range of production sectors, from manufacturing to energy production, and including military and logistics domains.
Our mission is to safeguard essential operations, ensuring that critical activities can continue without interruption, regardless of the sector.
Our team of experts combines advanced technical expertise with a deep understanding of OT environments, delivering state-of-the-art threat monitoring solutions, customized to meet each client's specific needs.
MON5 is committed to preventing downtime and mitigating risks associated with emerging cyber threats, ensuring operational continuity and resilience of critical infrastructures.
discover
Our Solutions
Asset Discovery
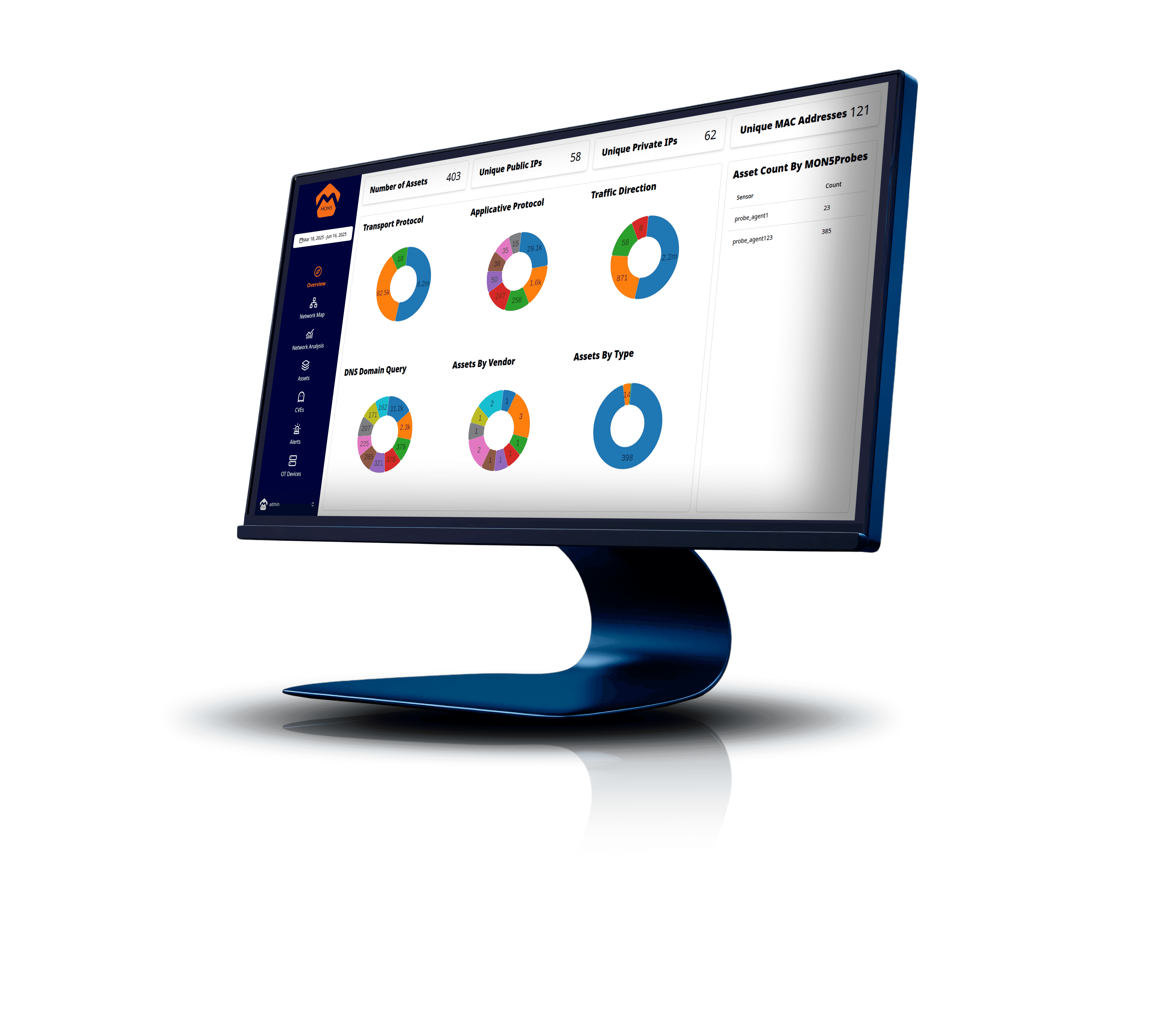
Generate your plant map for a complete view of all assets! Identification and cataloging of all devices and systems present in the OT infrastructure, ensuring complete and up-to-date visibility of company assets.
OT Compliance
Make your infrastructure compliant with the new European NIS2 directives, with particular emphasis on network structure and segmentation, ensuring your organization meets the cybersecurity standards required for critical infrastructures.
OT Monitoring
Keep your OT infrastructure under control in real-time! Continuous detection of network activities and events to identify anomalous behaviors, threats, and malfunctions. Constant monitoring enables timely intervention, reducing risks and improving operational resilience.
OT Vulnerability
Identify and fix your OT network weaknesses before they can be exploited! Proactive analysis of vulnerabilities present in industrial devices and systems, with risk-based prioritization. A targeted approach to strengthen security and protect the most critical assets from potential attacks.
How MON5 Works
MON5 solutions offer three fundamental approaches to ensure OT network security:
These approaches enable proactive security management, ensuring continuous protection of critical infrastructures.
CONTACT US
HOW MON5 OPERATES
To ensure effective protection of OT infrastructures, MON5 adopts an integrated approach combining hardware probes with centralized management and hybrid active and passive monitoring.
Hardware Probes with Central Management
Complete Visibility: Our hardware probes, strategically distributed within the plant network, enable real-time identification and classification of all IIoT devices, OT systems, and connected IP systems, whether managed or unmanaged. This approach provides detailed and up-to-date mapping of network assets and ensures a TOTAL and COMPLETE view of the plant.
Active/Passive Approach
Continuous Monitoring: Through constant analysis of network traffic and OT device behaviors, our solutions provide real-time monitoring. The passive approach involves observing traffic without interference, while the active approach includes direct device interrogation when necessary, to obtain more detailed information and ensure timely response to potential threats.
This combination of technologies and methodologies allows MON5 to offer advanced and customized protection,
ensuring the security and resilience of our clients' critical infrastructures.
INTEGRATIONS
MON5 is designed to seamlessly integrate with major systems used in industrial environments, including leading brands such as Siemens, Allen-Bradley (Rockwell Automation), Schneider Electric, and Omron.
If your network includes devices currently not present in our extensive database, don't worry: we are committed to rapidly implementing support for such devices, ensuring optimal compatibility and complete protection for your infrastructure.
SECTORS
MON5 offers cybersecurity solutions for a variety of industrial sectors, each with specific needs:

Aerospace
Companies producing satellite components rely on advanced digital systems. Protecting them from cyber threats is essential to ensure operational continuity, intellectual property protection, and the success of space missions.
Manufacturing
Production lines often include machinery of different ages and technologies, creating a heterogeneous environment. This diversity can introduce vulnerabilities that require careful management to ensure security and operational efficiency.
Automation
Automation systems, while improving efficiency, can become obsolete over time, increasing vulnerability to cyber attacks. Addressing these challenges is essential to maintain security and operational continuity.

Energy
Energy infrastructures are frequent targets of cyber attacks. Safeguarding these structures is essential to maintain reliable energy supply and prevent disruptions that could have significant consequences.
MON5 is designed for all contexts where machinery, PLCs, and connected work centers operate.
It offers customized solutions to address specific industrial cybersecurity challenges, ensuring the protection and resilience of critical infrastructures.
CONTACT US
Together we'll understand the best process to protect your infrastructure
